Experts have detected a serious vulnerability in PHP, which is frequently employed in popular web servers like XAMPP. The flaw, assigned the identifier CVE-2024-4577, enables cybercriminals to remotely execute malicious code on Windows devices.
Easy Vulnerability Exploit
Cybersecurity experts state that the flaw can be easily exploited, taking advantage of a Windows built-in feature, Best Fit. This feature incorrectly converts some Unicode characters in PHP, enabling hackers to perform arbitrary commands using an argument injection technique, according to a report by Ars Technica.
PHP Versions at Risk
The vulnerability affects PHP versions operating in CGI mode in which the web server forwards HTTP requests to the PHP interpreter for handling. However, even installations not using CGI mode are susceptible if they have externally available PHP executable files. This configuration is enabled by default in XAMPP for Windows, a well-known software bundle.
Demonstration of Exploit Tactics
Researchers demonstrated how a benign HTTP request can be converted into a command for launching a PHP interpreter with additional arguments. These arguments can authorize remote PHP code execution from the body of the request. Input values would make use of the following argument injection: ‘-d allow_url_include=1 -d auto_prepend_file=php://input‘.
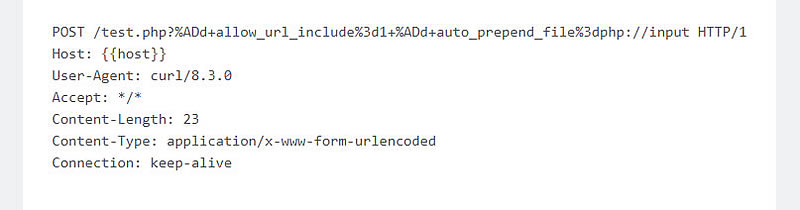
A confirmation of a successful RCE would appear on the phpinfo.php page, thus circumventing the CVE-2012-1823 vulnerability protection established in 2012.
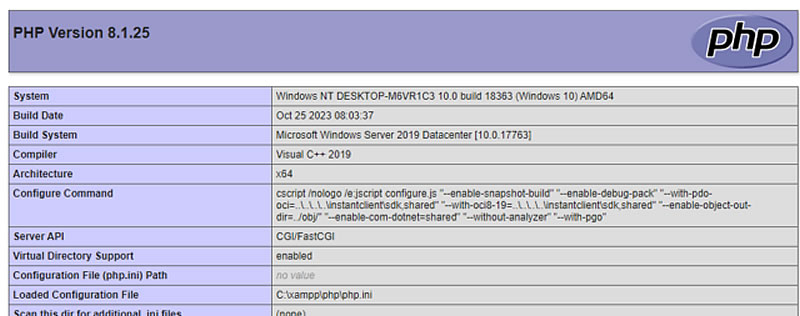
Response and Fix
After publishing the vulnerability details, the cybersecurity organization Shadowserver conducted an internet scan and discovered thousands of compromised servers. Given the simplicity of the attack and PHP’s wide prevalence, experts urge administrators to urgently patch their systems to avoid potential attacks.
The vulnerability was discovered by Orange Tsai of Devcore during a PHP security audit. PHP developers released a fix on the same day the vulnerability was reported, on Thursday, June 6. Despite its triviality, Tsai contends that this type of error is of great interest for research.





