AMD Reports High-risk Vulnerabilities in Multiple Processors
Semiconductor manufacturer AMD has announced four high-risk vulnerabilities according to the CVE classification, affecting a range of its processors. The issues span from Zen architecture chips to Zen 4 architecture models. A fresh BIOS firmware addressing these security issues is now available for many of the processors.
The vulnerabilities, termed CVE-2023-20576, CVE-2023-20577, CVE-2023-20579, and CVE-2023-20587, expose the SPI interface on the processors, facilitating their interaction with BIOS chips on motherboards. These vulnerabilities are potential targets for denial-of-service attacks and even remote execution of arbitrary codes. However, local access to the PC with an at-risk processor is required for these threats to materialize. Not all AMD chips from Zen–Zen 4 architectures are vulnerable to these four specific security threats.
Patching the Vulnerabilities
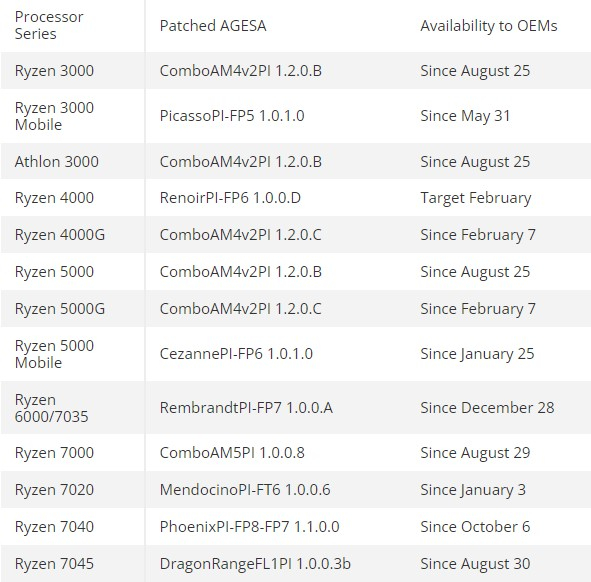
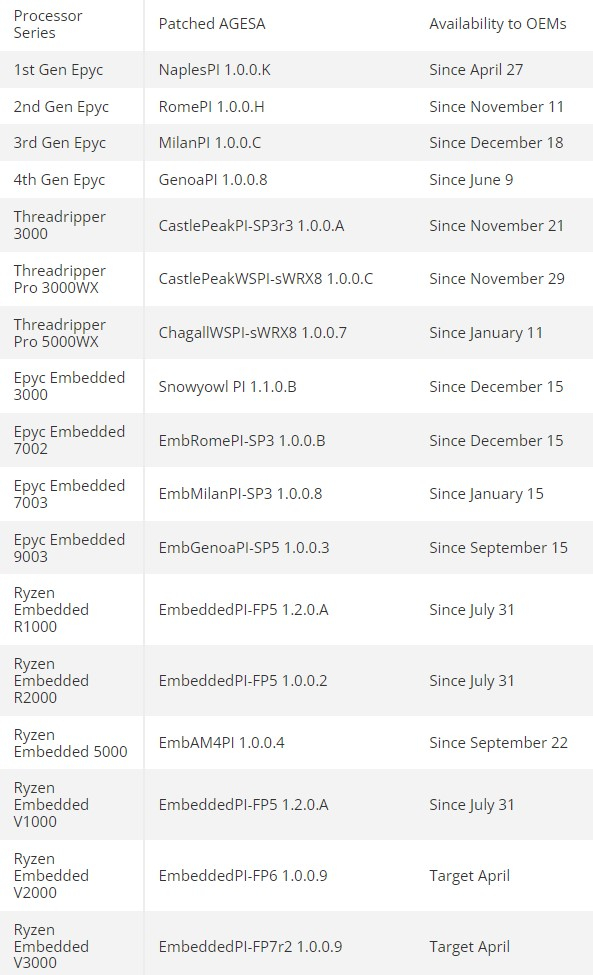
AMD is addressing these security gaps with new AGESA library versions, the foundations of the motherboard’s BIOS firmware. Updated AGESA versions have been released by the company for most of its chips. The latest AGESA libraries for the Zen 2 architecture models also fix the Zenbleed vulnerability discovered last year. BIOS based on AGESA 1.2.0.B library is necessary to protect the same Zen 2 chips from the last four vulnerabilities, while AGESA 1.2.0.C library-based firmware is needed to rectify the Zenbleed vulnerability. Unfortunately, not all motherboard manufacturers have yet released new firmware with the corrected AGESA. Tables in the document display firmware versions for various AMD processor models with the mentioned vulnerabilities fixed.
Advanced Micro Devices’ Prevention Measures
Anticipatory measures have been taken by AMD for the EPYC processors, with their vulnerabilities addressed by AGESA versions released months ago. The Threadripper chips received the required updates in January. Interestingly, the Threadripper 7000 models are excluded from the list of affected processors, hinting at a potential preemptive fix of security problems. BIOS updates for Ryzen Embedded V2000 and V3000 processors, which are yet to receive the necessary updates, are expected in April this year.
Rollout of New AGESA Versions
New AGESA versions are circulated via new BIOS versions, which are developed by motherboard creators. This implies it may take a while for manufacturers to design new firmware versions based on AMD’s newly-released libraries for their motherboards. While the scale of the BIOS updates already launched for server, embedded, and mobile processor segments is arduous to gauge, an evaluation for consumer motherboards for Ryzen and Threadripper chips is possible. Tom’s Hardware analyzed the BIOS firmware release by four leading motherboard suppliers — ASUS, ASRock, Gigabyte, and MSI — to create such an assessment.
New Upgrades and Implications
It appears that AM5 Socket boards with AMD 600-series chipsets have received necessary security updates, implying that Ryzen 7000 and Ryzen 8000G processors have progressive immunity against the stated vulnerabilities. Reportedly, AMD is precluding Threadripper 7000 processors. Consequently, boards with TRX50 and WRX90 chipsets are provided with necessary protection.
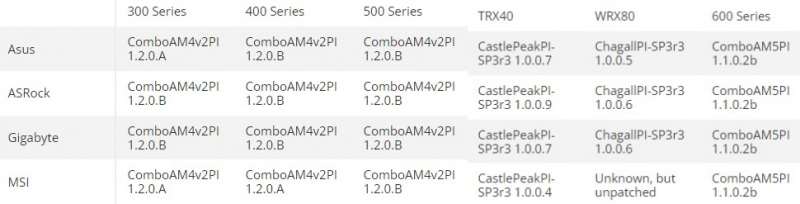
Regrettably, manufacturers are slow to release firmware upgrades for the previous generation AM4 Socket owners compared to the newer AM5 platform chips. According to Tom’s Hardware, none of the cited four plate manufacturers has yet to launch a BIOS based on the latest AGESA 1.2.0.C library. Consequently, Ryzen 4000G and 5000G series processors are subject to these vulnerabilities, irrespective of the board models and their producers. The most prevalent AGESA library version utilized for the AMD 500-series chipset is AGESA 1.2.0.B, with all four manufacturers providing a BIOS firmware based on it. ASUS and MSI boards with AMD 300-series chipsets are still leveraging the AGESA 1.2.0.A library, along with MSI boards on AMD 400-series chipsets.
Most TRX40 chipset boards for Threadripper 3000 processors are safe, but MSI boards are an exception, continuing to use the old AGESA 1.0.0.4 version in their BIOS. No BIOS updates have been released by manufacturers using a fresh AGESA version for Threadripper Pro 3000WX and 5000WX processors for the WRX80 platform.