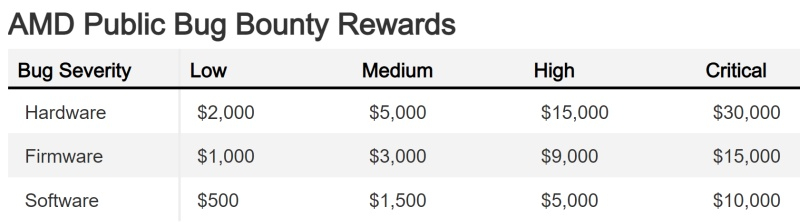
AMD, the multinational semiconductor company, has partnered with crowd-sourced security provider Intigriti to launch a Bug Bounty Program. Security researchers and ethical hackers can identify vulnerabilities or errors in AMD’s hardware, firmware, or software and report them via the Intigriti platform. Each identified bug will bring a financial reward ranging from $500 to $30,000 based on the severity of the issue.
Previously, AMD’s bug bounty program was available only to a select group of researchers. This new initiative will involve a wider community of testers and experts in looking for issues in AMD products. The rewards on Intigriti’s platform will depend on the seriousness of the detected error and the product category.
Researchers still have the option to report the issue directly to AMD via its product security team but using this route does not come with any guaranteed payment. However, the person who found the error will be mentioned in the security bulletin.
The implementation of bug bounty programs is vital for large tech companies like AMD whose products and services cater to millions of customers. Their products, especially AMD Zen 2 and Zen 3 processors, had been vulnerable to hacking via the security TPM module. Other notable incidents involve Inception vulnerability in AMD Zen 3 and Zen 4 processors, the Zenbleed vulnerability in Zen 2 based systems, multiple errors in the AMD AGESA library for the BIOS of AMD 600 series motherboards for Ryzen 7000 processors, and the hanging of the EPYC 7002 Rome server processors core.
Many other tech corporations, like Intel with its Project Circuit Breaker, also run bug detection reward programs to ensure that their systems and products are void of any hidden vulnerabilities.
Successful bug bounty hunters can earn substantially from these programs. In 2020, many ethical hackers made over $90,000 a year. In 2023, Google paid out at least $10 million in total bug discovery rewards, and Polygon Technology paid $2 million to a researcher who found a critical error.